To keep a company secure in today’s digital universe, it takes a village — specifically, all the company’s employees, who have to be on their guard pretty much all the time to avoid phishing, credit stuffing and other kinds of common attack vectors and techniques that lead to their data and that of their businesses being compromised. A London startup called Push Security believes it can help in that effort — not by blocking online activity and app usage, but by monitoring when users are making iffy choices with web-based apps and showing how to fix them. Today it’s announcing $15 million in early-stage funding to expand that effort.
The Series A is being led by GV (Google Ventures), with Decibel and a number of angels participating. (The individuals include Duo Security co-founders Dug Song and Jon Oberheide.)
The funding follows a $4 million seed and some notable signs of early traction. The startup says that since it launched in July 2022, its tools have been adopted by ‘hundreds’ of teams and some 50,000 users, with customers including Reachdesk, Upvest and Tray.io (whose founder and CEO Rich Waldron is also an angel investor in this round).
Adam Bateman, the co-founder and CEO of Push Security, said that he came up with the idea for Push after years of working as an ethical hacker and observing a lot of the most common errors and practices among employees.
One thing that came up time and again was the fact that no matter how strong a company’s security policies were — and no matter how much it invested in firewalls, endpoint solutions and the rest — human actions around bad password choices, inadvertently clicking on dodgy links, and unknowingly sharing things they’re not supposed to, often proved to be the first chink in the armor.
Push’s starting point is to accept that there are certain behaviors that will be second nature to people: namely, they will want to use web-based apps at work that help them work better, even if those tools have not been provisioned by IT. That has exploded as a trend especially in the last couple of years with more people working remotely and cloud-based architectures becoming the norm for them.
Push’s approach follows a few different tracks: it watches how those apps are used and then automatically “pushes” suggestions to employees when it spots them using those apps in less secure ways — say, by choosing easy-to-guess passwords; it “pushes” notifications to security and IT teams to give them summaries of activity so that they are kept in the loop; and it then adds the app to a dashboard for those teams to monitor and flags when those apps pose a danger because they in themselves may have security issues and bars those that might be downright dodgy.
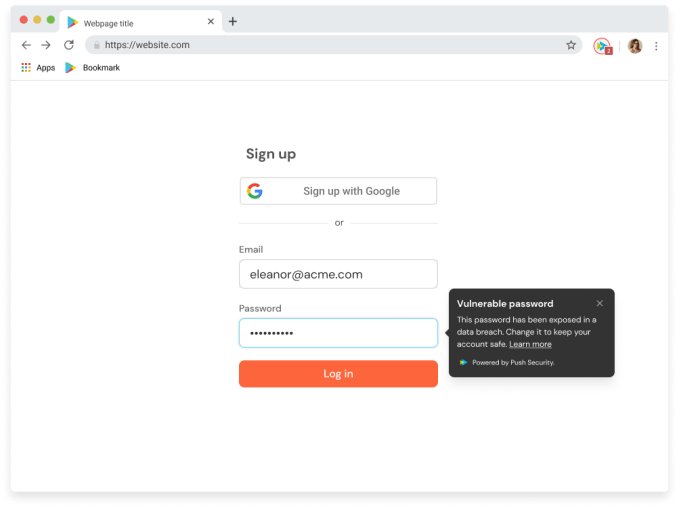
The key is that Push tries to be friction-free by not barring activity, but it enables better practices by pushing better suggestions to everyone.
Bateman likens its approach to that of Grammarly. “You don’t have to but it can stop you from making mistakes,” he said in an interview. “It’s the same with us. Push keeps you safe. A lot of work we do on the human level is not to be the enforcer, to be the guard rail not a gate.”
So while there are hundreds of companies in the market offering password management, app management, desktop management, firewalls, blacklists and whitelists, and more, what’s caught investors’ attention here is the idea of a tool that lets people continue to work as-is.
“The global workforce is moving toward greater freedom and flexibility with SaaS applications, which introduces new security complexities and challenges,” says Karim Faris, general partner at GV, in a statement. “That trend presents a critical need for better, simpler tools that engage employees and take the burden off centralized IT to manage SaaS sprawl. GV is excited to partner with the Push team as they help modern security teams navigate the evolving cybersecurity threat landscape.”
All of this operates currently for employees who are already using Office 365 or Google Workspace emails to manage their log-ins to apps they use for work, Bateman said. If someone tries to sign up for a work app using a non-work email, that too is flagged.
Push Security is designed just to work on desktops and laptops — not mobile. That’s because mobile device management, which typically includes apps and other mobile usage, is already a very well-covered area. More murky are desktops where people can download SaaS from the internet very easily.
The growth of SaaS has opened up a new world of productivity for workers, but it’s also opened up a can of security worms. Given that a lot of apps ask to “access your contacts” and other data in order to work most effectively (which is why so many log in with their work credentials in the first place), it creates a potential data leak if those accounts are not subsequently managed responsibly.
In Push’s research, it found that 23% of Microsoft integrations, and 17% of Google integrations monitored through its platform “granted access to high risk assets and data such as email, calendar, and shared drives” and as a measure of how many places people are using these credentials, among Microsoft app integrations, only one-third were approved by IT via OAuth. (The other two-thirds, Push said, were provisioned “directly by employees with no IT oversight or visibility.”) It didn’t provide corresponding data for Google-based app integrations.
Push says it has added close to 500 SaaS apps to IT dashboards since it was launched less than a year ago. In other words beyond the most popular, or approved apps used by its customers, there have been another 500 collectively picked up organically by employees across that customer base, representing a potential leakage nightmare.
Push Security raises $15M to help SaaS users lower their online vulnerability by Ingrid Lunden originally published on TechCrunch








